Lab 1: Discover¶
In Lab 1, you will enable the discovery features of Valtix and gather inventory and traffic information about your AWS account
Procedure¶
- Ensure you have completed the prerequisites
- Log in to Valtix Dashboard
- Navigate to Getting Started -> Easy Setup -> Cloud Account on the left panel
- Click on the AWS logo. This will take you to the onboarding page to link the Valtix Controller with your AWS account.
- To onboard your AWS account, there are 2 steps:
- Deployment of CloudFormation template to create necessary IAM permission for the Valtix Controller - step 6
- Provide information to onboard your AWS account with the Valtix Controller - step 11
- Click on the CloudFormation link at the top of the page. This will open a new browser tab for the deployment of the CloudFormation template in your AWS account. You may asked to log in to your AWS account.
-
In the CloudFormation template, most of the mandatory fields have been auto-filled. Provide the following parameters:
Parameter Description S3 Bucket Name Supply a unique S3 bucket name. This bucket name needs to be globally unique in AWS. See bucket naming rules VPC ID This VPC ID is the spoke VPC ID. If you deployed CFT in pre-requisite section for this lab, you can find this information in the stack output. -
Select the checkbox "I acknowledge that AWS CloudFormation might create IAM resources with custom names", and then click Create Stack.
- Wait for the CloudFormation stack to complete. This may take a few minutes.
- Navigate back to the Valtix Controller browser tab. You should still be on the onboarding page where you clicked on CloudFormation template link.
- Provide information to onboard your AWS account with the Valtix Controller. Most information is filled in already. Below are 2 parameters you need to fill in.
| Parameter | Description |
|---|---|
| Account Name | Provide your account name |
| Controller IAM role | This information is given in the CloudFormation stack output. Look at the value for ValtixControllerRoleArn in the output tab. |
Verification¶
- Navigate to Discovery -> Inventory -> Summary. This page provides a list of cloud resources that were discovered by Valtix. You can see everything in your account on a single page.
-
Now generate traffic to see DNS and VPC information: a. SSH to the EC2 instance created in the spoke1-vpc. Default username is centos. (eg.
ssh -i <private_key.pem> centos@<ec2_eip>) b. Generate traffic to following website:curl http://www.google.com curl http://www.facebook.com wget -O /dev/null -o /dev/null http://purplehoodie.com -
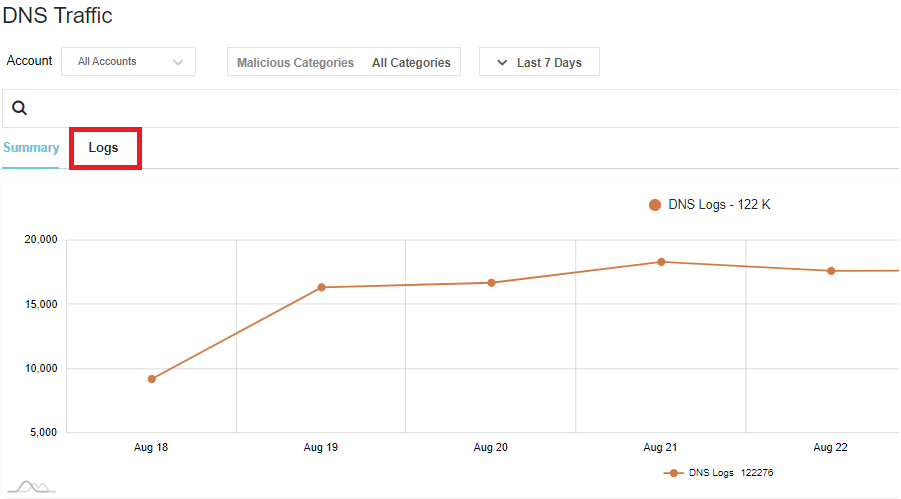
Navigate to Discovery -> Traffic -> DNS
- This provides a summary of the traffic that Valtix gathered from DNS query logs.
-
Click on Logs. You should see the traffic that you generated to Google and Facebook.
-
Click on Malicious Categories. If Valtix detects any traffic that could potentially be malicious, Valtix highlights those user sessions. Navigate back to Summary. This provides a better view to see malicious activities.
- The traffic generated to purplehoodie is a potential malicious site categorized by Brightcloud. If you lookup purplehoodie.com in brightcloud url-lookup, you'll see that it's high risk.
- Navigate to Discovery -> Traffic -> VPC
- Through VPC flow logs, Valtix provides a summary on VPC traffic and where it is connecting to