2.9 Features and Changes¶
Welcome to the features and changes for release version 2.9. Valtix product, engineering and testing teams have been hard at work bringing many valuable enhancements to the solution. We’re excited to share the list of significant features to help guide you through what to expect with the new release.
We will also cover the changes introduced to bring awareness, what to expect with each change, how it differs from previous release behavior and the value it brings with its use.
We hope you enjoy the new features as we are very proud of the hard work that has gone into making them a reality and bringing them to you, our customer. If you have any questions on the new release, please reach out to Valtix Customer Support. We would be happy to assist.
Release Features¶
- Easy Setup
- Multi-Cloud PaaS Visibility and Control
- Flexible Multi-Cloud and Multi-Account Dynamic Security Policies
- Group Address Object
- Protect Unsecure VPCs
- Cloud Visibility Report (CVR) - Threat Indicator Snapshot
- Visibility of Out-of-band Traffic in Azure and Google Cloud
- New Navigation Menu and Search
- Sample Policies and Profiles
- Unified Log Action Terms
- Gateway Page Redesign
- Ruleset Summary Page Redesign
- Resource Check on Min and Max Instances
- System Page Redesign
- Terraform Improvements
Click Here for more details about the release
Release Changes¶
New Look and Feel¶
The Valtix UI team has been working diligently to enhance the look and feel of the Valtix Controller UI. This is one of many steps that will bring more workflows, usability improvements, and overall an enhanced interactive experience to ensure security in the cloud is simple and robust.
In the new release, Valtix has introduced the following UI look and feel changes:
- Top level menu items seen in 2.8 (Dashboard, Discovery, Investigate, Manage, Settings) have been moved to a common left-positioned navigation pane. With this change, the items that were only accessible by clicking on the top-level menu items are shown as sub-categories under each top-level category. The objective is to make navigating to the category of interest be direct, requiring fewer clicks. The navigation categories can be collapsed to provide a more concise view and expanded as needed.
- A dynamic menu Search has been introduced that operates on the menu items to quickly filter the menu to what has been specified in the search. The menu will dynamically change based on the characters typed into the Search string.
- A top-5 Recent Visits is now available to present commonly selected menu items. The Recent Visits list will always be visible.
- A Getting Started menu category is introduced with an Easy Setup workflow for onboarding a CSP account, creating a Service VPC and deploying a Valtix Gateway.
- A new Reporting menu category is available to create Cloud Visibility Reports (CVRs). These reports have been enhanced to operate against CSP Discovery based on VPC/VNet flow logs and DNS query logs, as well as Threat Indicators based on the traffic seen by the Valtix Gateway.
Gateway Management¶
Managing Gateways is a part of maintaining security and ensuring the environment is leveraging the latest and most advanced protection. Managing and maintaining security needs to be simple and quick, and any changes need to have nothing but a positive impact on the operational environment with zero downtime. Valtix has enhanced the management and maintenance of Valtix Gateways through improvements to the UI. This is the first of many enhancements to eventually make bulk operations possible and to accommodate automating the process to the likes and desires of the administrator.
In the new release, the Manage Gateways UI changes include the following:
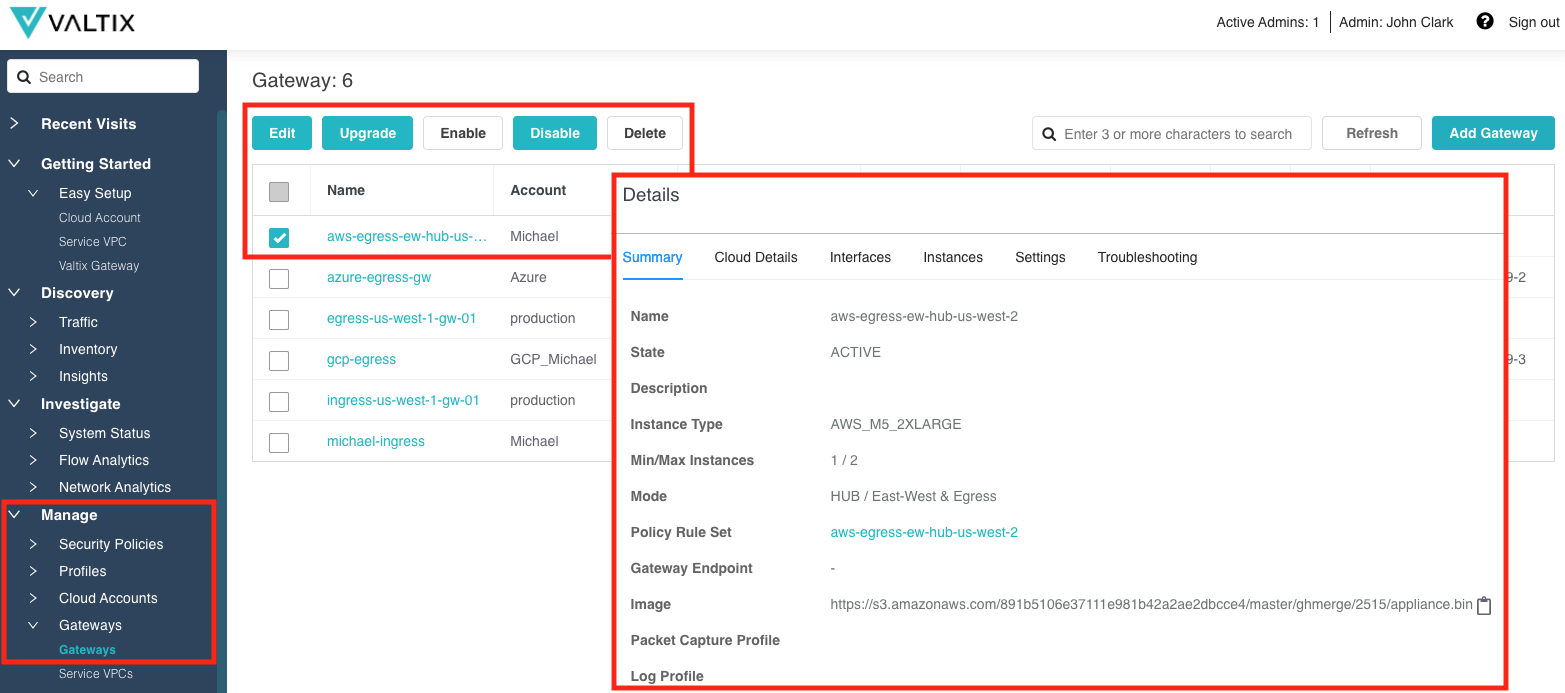
- Eliminating the “hamburger” stack that provided common operations to the Gateway (Edit, Upgrade, Disable, Tech Support, Troubleshoot) and moved some of those operations to menu items above the list of Gateways. Bulk operation is not yet available, but will be part of a future release.
- Selecting a Gateway exposes the Details, which has been enhanced to provide an easier way to view the Gateway (Summary, Cloud Details, Interfaces, Instances, Settings, Troubleshooting). Each category has been enhanced to provide valuable information about the Gateway as it relates to the specific category.
- Gateway Troubleshooting has been moved to the Details and has an enhanced organization. This proves useful when investigating the Gateway and Services VPC relationship and configuration.
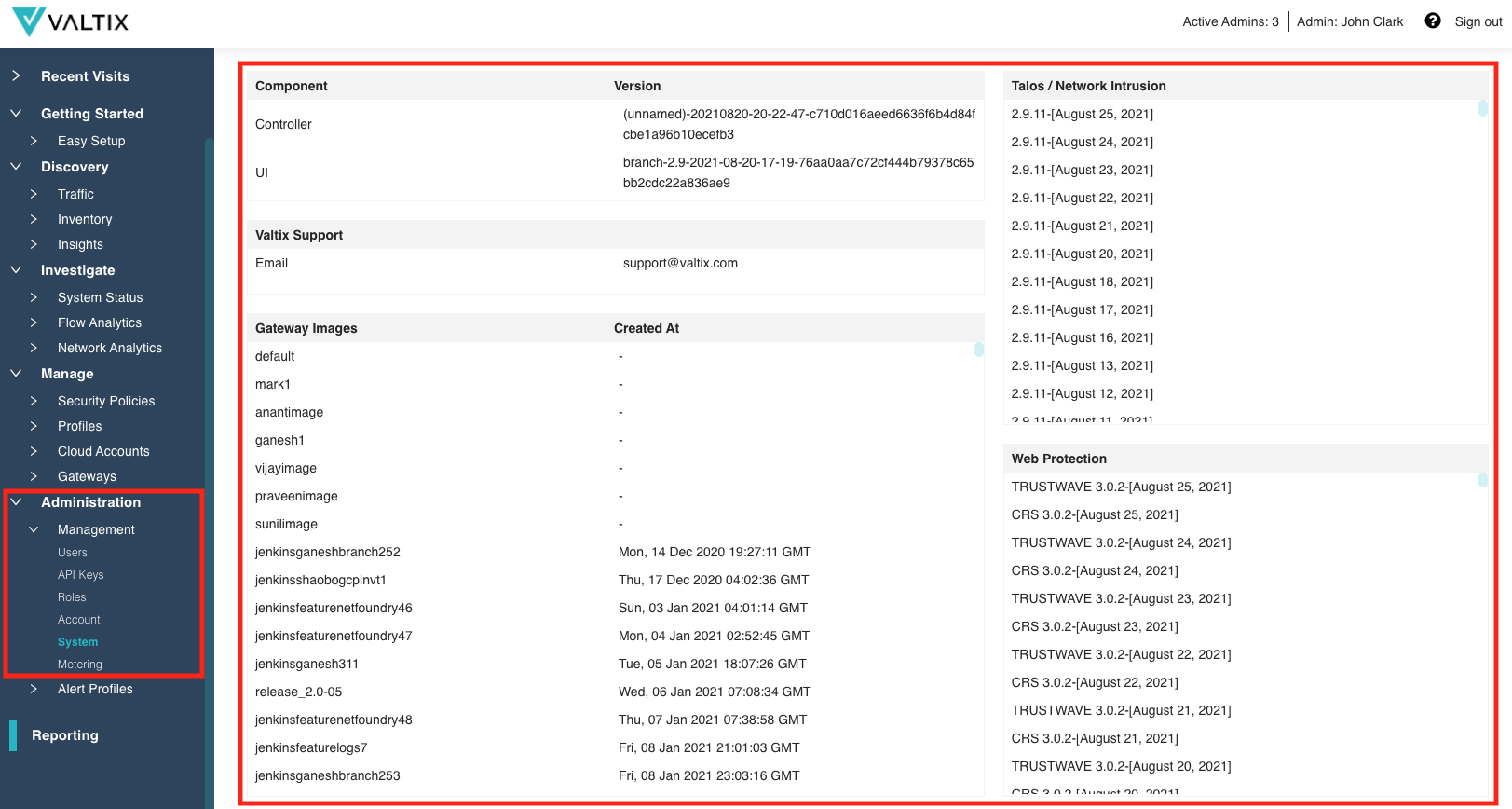
System Management¶
Valtix has enhanced the System Management information and how it has been displayed. The System details provide information on the Controller, UI, Gateway Images, and security profile ruleset updates (Talos, Trustwave, CRS). The information is displayed in a more consumable way, and is used to provide an understanding of the system in use, and what has been published and made available by Valtix.
Cloud Resource Check¶
When deploying a Valtix Gateway stack into a cloud account, it’s important to ensure the service quota limits and their resource availability are configured to accommodate minimum (initial) deployment and maximum deployment. This check is performed during the Review step of a Gateway deployment prior to initiating the deployment.
In the new release, the resource check provides a more granular view of the limits, what is used, what is needed for a minimum (initial) deployment and what is needed for a maxim deployment (auto-scaling).
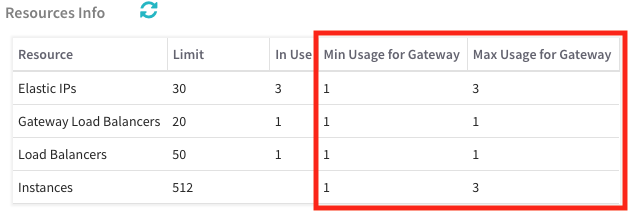
The limits and availability does not inhibit a deployment, but provides valuable information to aid in a deployment consideration. It is highly recommended to increase the limits and ensure availability exists to meet the needs of maximum deployment. Otherwise the operational environment will be hindered if maximum deployment is necessary.
Unified Logging Actions¶
Logging traffic and events is an important way to view what is permitted or denied, and what malicious activity is detected and inhibited. The new release unifies the logging naming convention and applies this convention across all locations where logging configuration is specified.
| Policy Rules | Network Threats | WAF | URL | FQDN |
|---|---|---|---|---|
| Previous Release | ||||
| Allow Log Allow No Log Deny Log Deny No Log |
Alert Drop Silent Drop |
Detect Block |
Allow Allow No Log Deny Log Deny No Log |
Allow Log Allow No Log Deny Log Deny No Log |
| New Release | ||||
| Allow Log Allow No Log Deny Log Deny No Log |
Allow Log Deny Log Deny No Log |
Allow Log Deny Log |
Allow Log Allow No Log Deny Log Deny No Log |
Allow Log Allow No Log Deny Log Deny No Log |
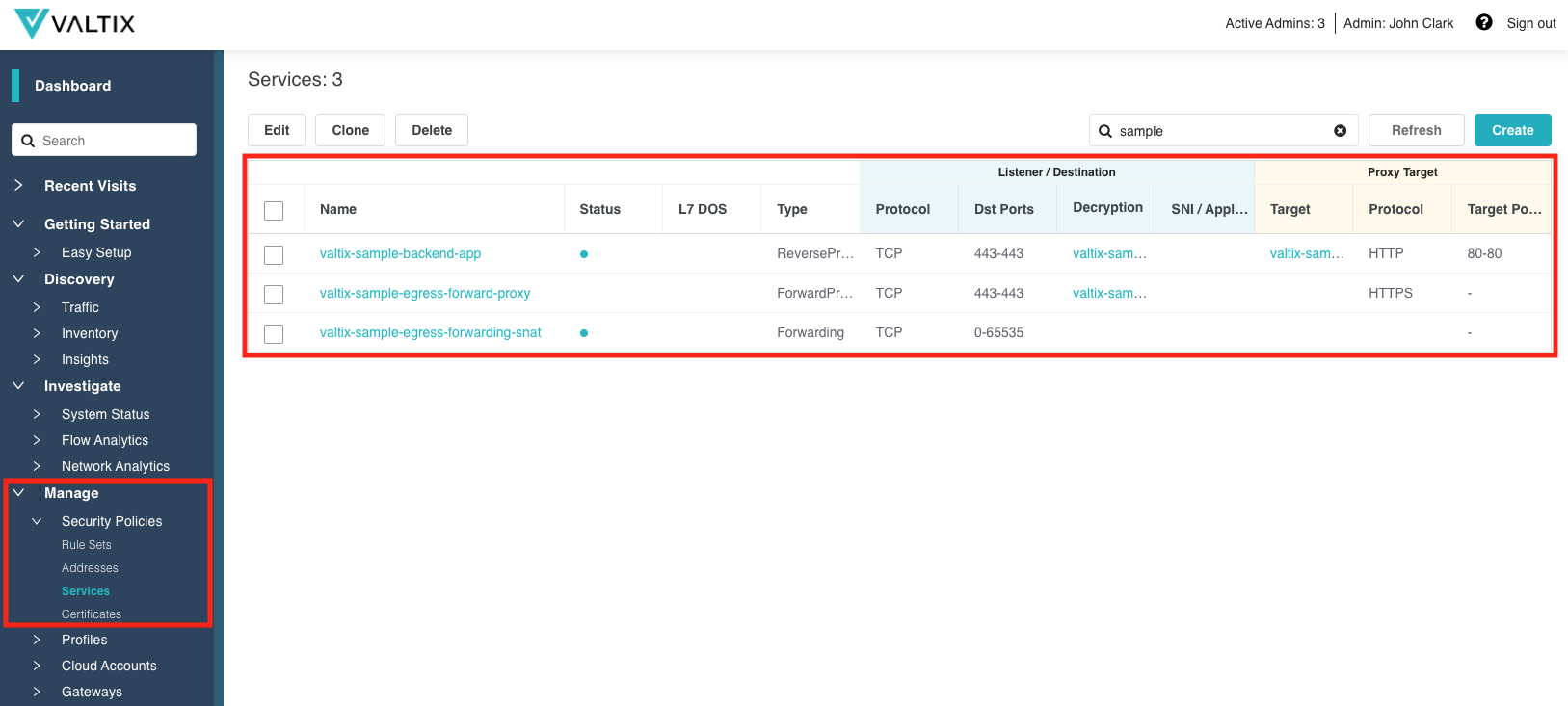
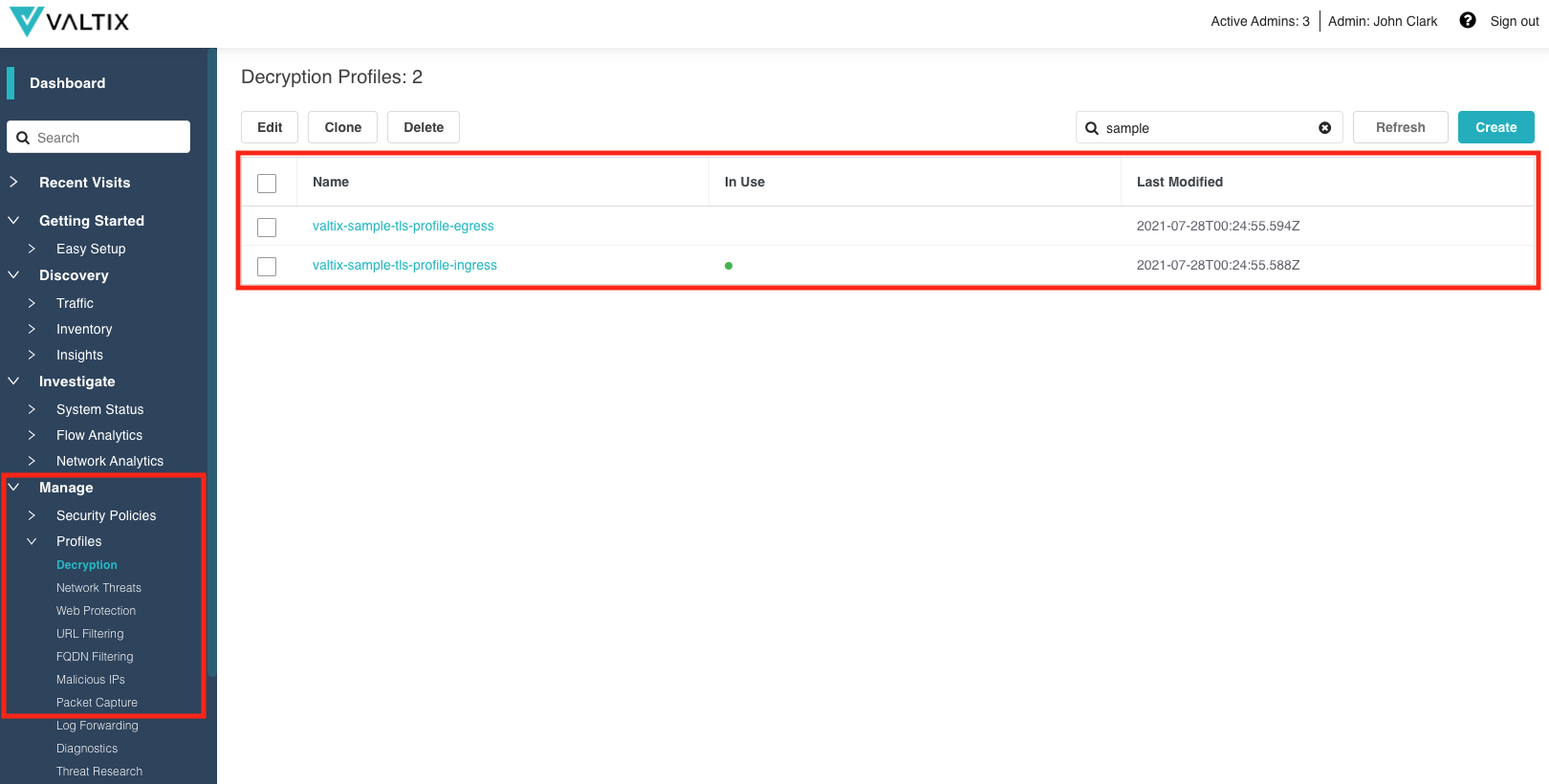
Sample Policies and Profiles¶
Valtix has made it easier to deploy by providing a starting point security that can be refined and enhanced over time. The new release will ship with a set of sample Security Policies (Rule Sets, Address Objects, Service Objects, Certificates) and Profiles (Decryption, Network Threats, Web Protection, URL Filtering, FQDN Filtering, Malicious IPs). These samples, which have a name that begins with “valtix-sample”, can be modified, cloned or replaced as the configuration is refined and enhanced.
The following are the list of available samples related to each category:
- Security Policies
- Rule Sets
- valtix-sample-ingress-policy-ruleset
- valtix-sample-egress-policy-ruleset
- Address Objects
- valtix-sample-backend-app
- Service Objects
- valtix-sample-backend-app
- valtix-sample-egress-forward-proxy
- valtix-sample-egress-forwarding-snat
- Certificates
- valtix-sample-tls-cert-egress
- valtix-sample-tls-cert-ingress
- Rule Sets
- Profiles
- Decryption
- valtix-sample-tls-profile-egress
- valtix-sample-tls-profile-ingress
- Network Threats
- valtix-sample-ips-balanced-alert
- Web Protection
- valtix-sample-waf-crs-detect
- URL Filtering
- valtix-sample-malicious-urls
- FQDN Filtering
- valtix-sample-malicious-fqdns
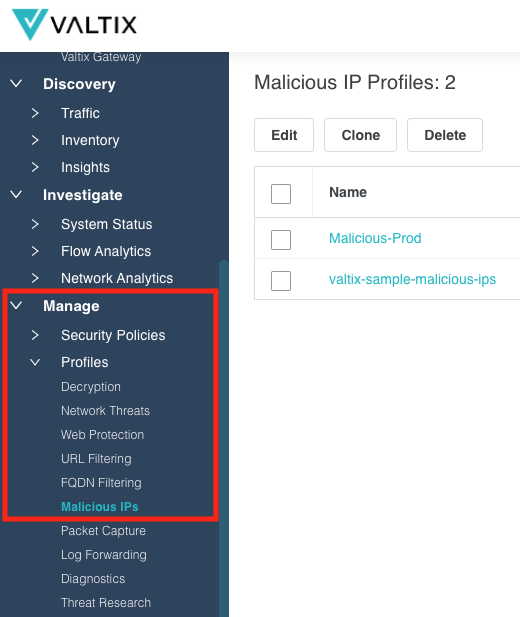
- Malicious IPs
- valtix-sample-malicious-ips
- Decryption
Malicious IPs¶
Malicious IPs are a set IP addresses that are known to be associated with malicious activity. The set of IPs come from Trustwave, the leading cybersecurity and managed security service provider focused on threat detection and response. Valtix integrates with Trustwave to provide one of many threat feeds used for advanced security. The Malicious IPs are updated dynamically and regularly as Trustwave continually refines their threat feed.
Malicious IPs can be both a source and a destination for malicious activity. In the new release, Valtix has expanded the use-case for Malicious IPs to support the Egress use-case, where a Malicious IP can be a destination of traffic and not purely a source of traffic.
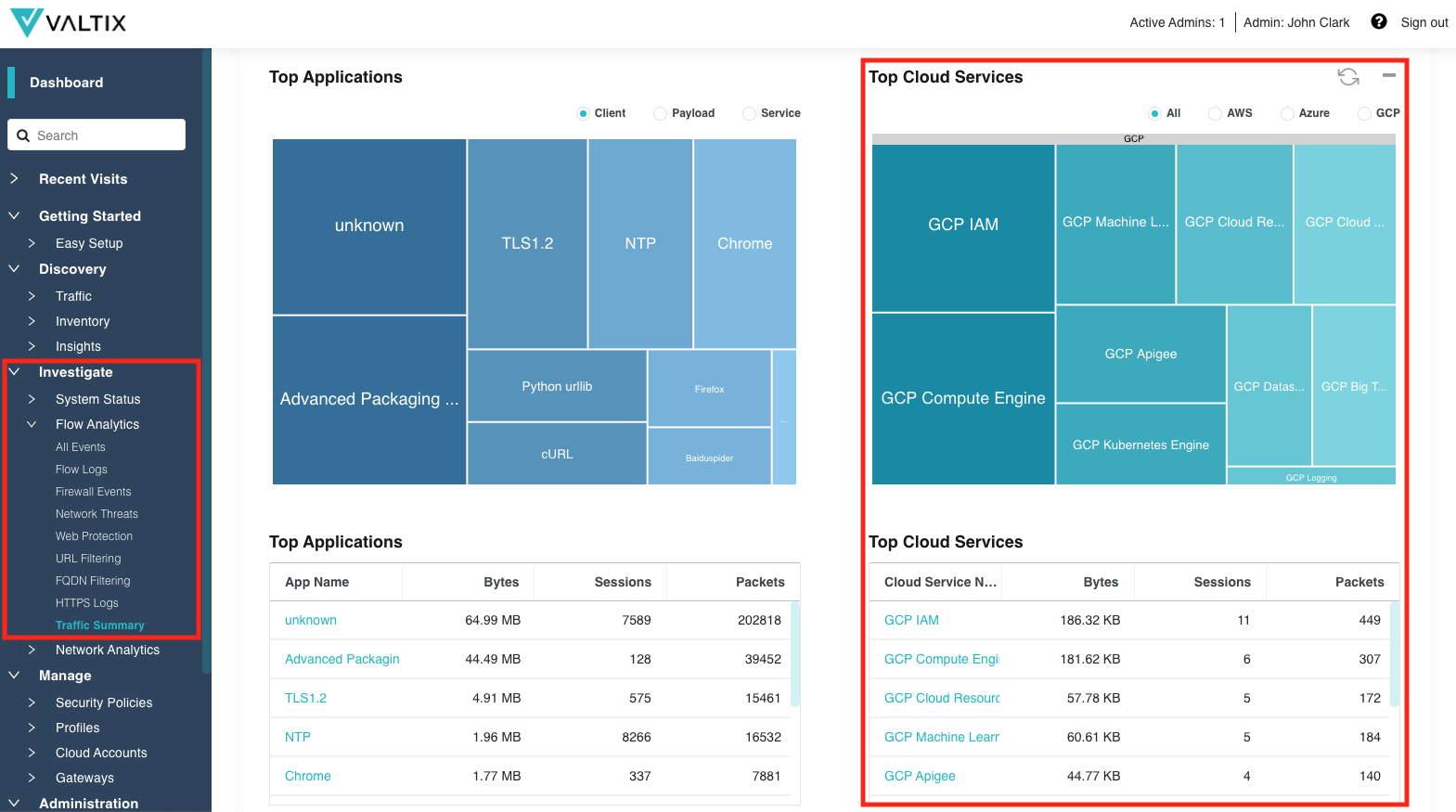
PaaS Visibility and Control¶
An important part of Valtix is its ability to integrate with the cloud accounts to discover cloud-related information (assets, traffic, DNS queries, cloud services, etc.), and to use that information to aid in deploying Valtix and in protecting against malicious activity. One of the many use-cases of discovery is to be aware of what traffic is related to the services offered by the cloud providers to know which services are being consumed. Having this information provides awareness and also aids in control over what services should be permitted and what services should be denied.
In the new release, Valtix has enhanced the Cloud Services visibility by extending it to cloud services offered by Azure and GCP.
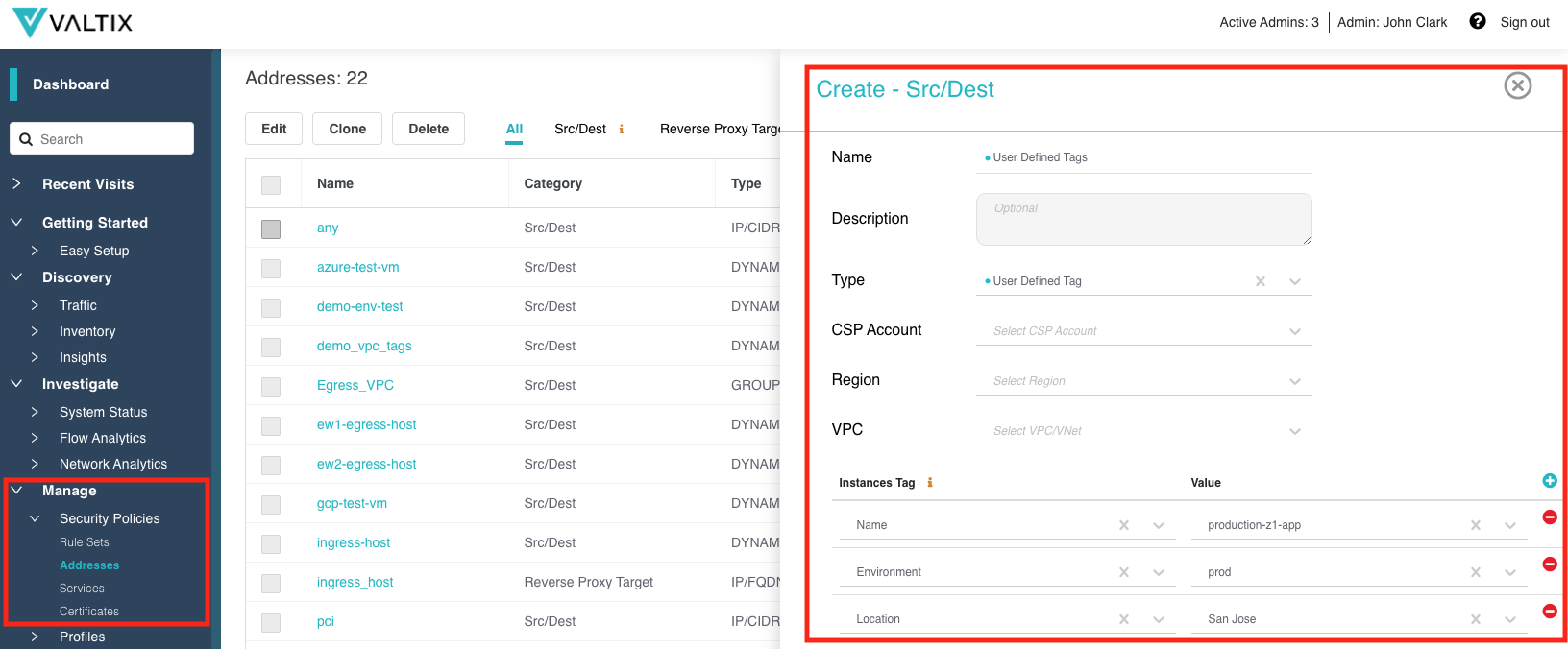
User Defined Tags¶
Valtix specializes in using cloud constructs to define dynamic multi-cloud policy. User-defined Tags is a powerful concept and leveraging these Tags to define security policy makes securing in the cloud easy, dynamic and scalable. User-defined tags are used in Address Objects as a dynamic way to map resources using a set of Tags to their IP addresses.
In the new release, more than one Tag can be specified per Address Object. If more than one Tag is specified, an AND operator will be applied. Resources that meet the cloud CSP, region and VPC specification and contain all specified Tags will be included in the Address Object.
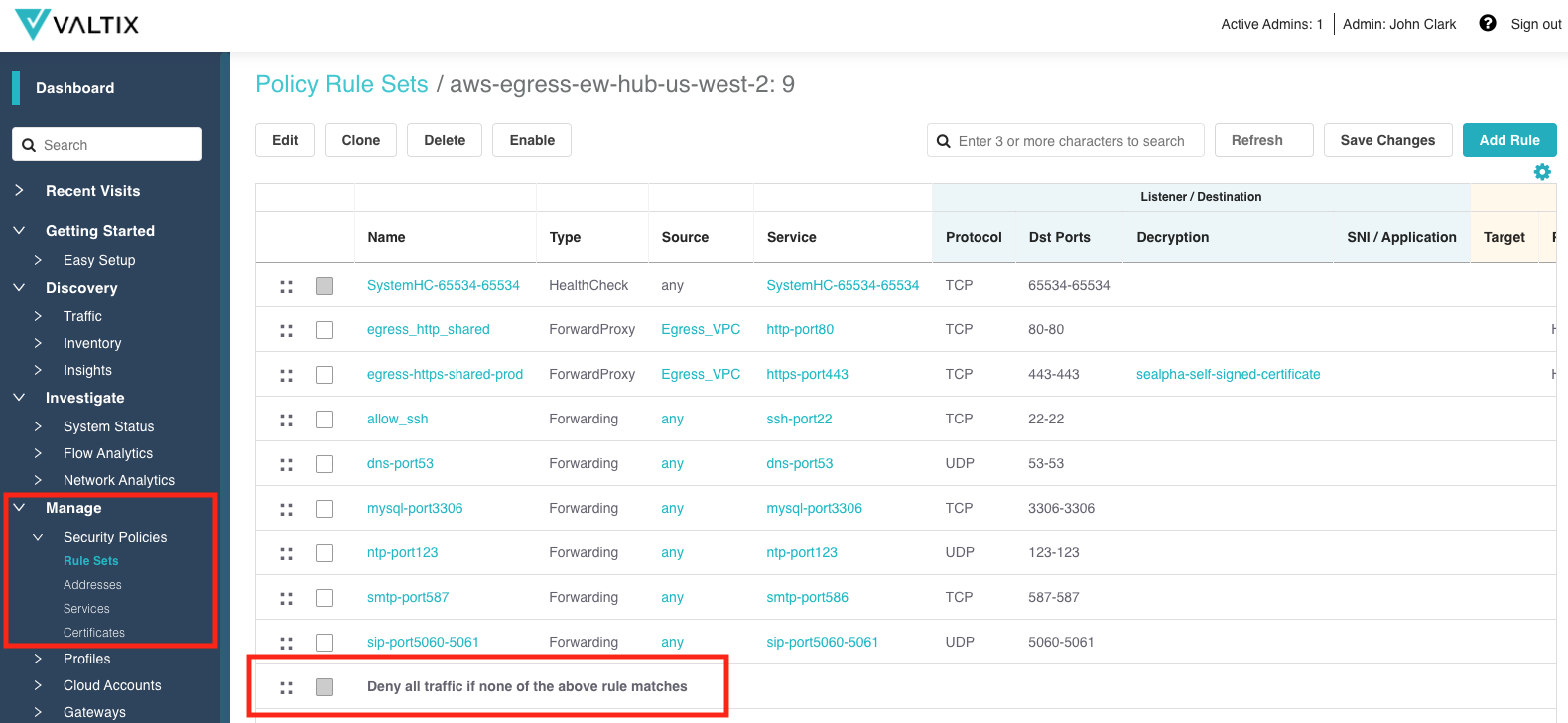
Explicit Deny All Rule¶
A Security Policy Ruleset is a fundamental way of defining a security policy that is applied to one or more Gateways. Each Rule within a Policy Ruleset evaluates traffic to determine a match. If a match exists, then the traffic will be processed based on the configuration of the Rule. If a match does not exist, then the next Rule is evaluated. If no rules match, then the traffic would be denied without logging based on an implicit (not visible) Rule.
In the new release, Valtix has enhanced the Ruleset view to make the implicit Rule an explicit (visible) Rule. This Rule cannot be edited nor can it be moved, disabled or deleted. It is there to make the Ruleset behavior clear. If there is the desire to alter this Rule to change its behavior (Deny to Allow, No Log to Log), a new Rule should be created as the penultimate Rule. The new Rule, being user-defined, can be edited, changed, disabled or deleted as desired.